Manage Risks & Accelerate Compliance
Federal Compliance Assessment Services
Comprehensive Federal Compliance portfolio – which is backed by the industry’s most tenured audit and advisory team – spans business case development to ongoing management.
End to End-managed Federal Compliance and Certification
Leveraging our proven expertise gained from providing federal certification advisory services to more than 4,000 organizations, we help you plan and execute a seamless journey tailored to your requirements. Our approach is built on years of experience supporting organizations of all types as they pursue the FedRAMP and DoD marketplace.
E Secure 360’s comprehensive federal portfolio, including FedRAMP (NIST 800-53r4), CMMC (NIST SP 800-171), CCPA, FFIEC, NYDFS, CJIS, DoD RMF, and FISMA, is backed by the industry’s most tenured audit and advisory team. It spans business case development to ongoing management.


E Secure 360’s approach
Our approach to helping you achieve and maintain certification comprises three activities: gap analysis, readiness preparation, and documentation development. Our FFIEC Certification methodology provides financial institutions with a framework that helps them measure their inherent risk profile and their information security maturity.
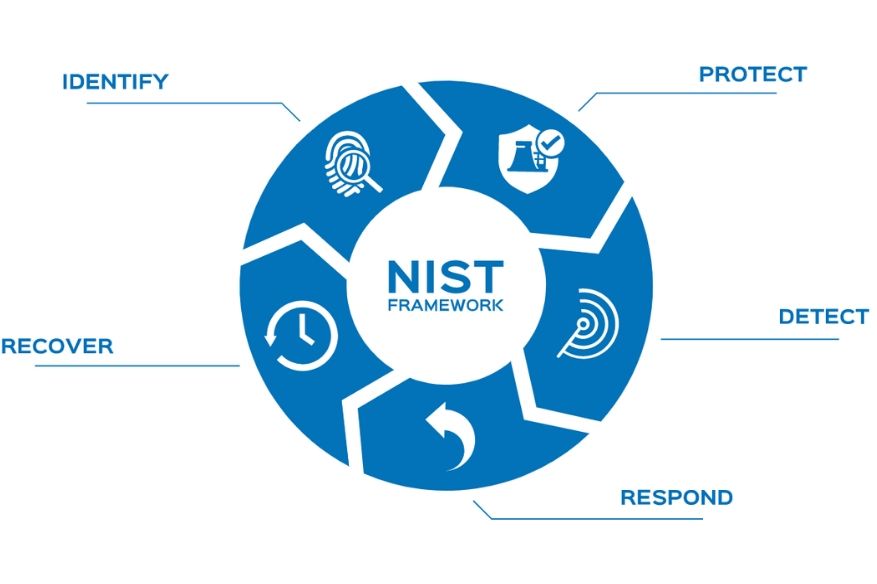
Address the NIST requirements
E Secure 360’s combined NIST Advisory and Cyber Engineering teams have developed a process to enable cloud service providers to be audit-ready in less than six weeks and at a fraction of historical costs. We view all companies as being on a journey to appropriately understand and address their cyber risk. The journey has three phases:
How can we help?
Our approach to helping you navigate the journey to Federal certifications comprises three activity groups: readiness, initial, and annual assessment.
Expertise – When You Need It
what people are saying
See how clients are future proofing their security and Stay ahead of disruption
with PCI Compliance Services

PCI Compliance Services helped us shift to a proactive security stance against threats and meet compliance requirements, giving us greater confidence in our ability to respond to cybersecurity threats faster and more effectively.
Peter Mayers – CEO Quantra Healthcare

PCI Compliance Services deep expertise in cyber procedures and standards identified gaps in our incident response plan and improved our ability to respond to a potential incident.
Smith Ares – CTO Linctron Financials
Unparalleled cybersecurity compliance experts
For more than 20 years, we’ve been at the forefront of compliance with the ability to coordinate and streamline the broadest set of compliance requirements in the industry.
Get Started
Get in touch with us.
We’re here to help.
Learn more about how our specialists can tailor a security program to fit the needs of your organization.








