Research-driven methodologies
Three-tier Mobile App Security Approach
Threat Centric Approach
Explore weakness as a hacker and demonstrate the potential consequences.
Comprehensive Report
Detailed description of security posture along with Risks, threat exposure and remediation plan.
Accurate snapshot
Coverage of business logic and vertical/horizontal authorization issues.
Advanced tools and techniques
E Secure 360 has been building and refining methodologies to assess the security posture of applications built across the varying platforms and languages used in decades worth of development. These methodologies map to proven OWASP standards while also accommodating the discovery of issues particular to your mobile applications, and web services. The goal is to:
- Provide risks in your mobile apps and helps you mitigate them through remediation guidance
- Find risks in client-side / server-side code, third-party libraries, or underlying mobile platforms
- Unique Behavioral analysis and privacy checks
- Supports all major smartphone platforms (including iOS, Android, Blackberry and Windows)

Research-driven methodologies
Minimise the risk to systems under test and cover all the vital areas.

Pricing Options
Strengthen your security operations posture and comply with the required compliance regulations.
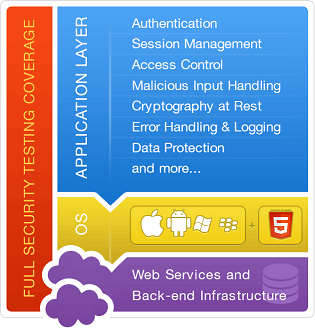
Three-tier Mobile App Security Approach
Mobile client assessment areas include: File system, Memory, Run-time tampering, Input validation, Source code analysis, Binary analysis and Inter-application communication.
Mobile network traffic assessment areas include: Transport layer security, Data stream analysis, Malware analysis and Host communication enumeration.
The web server side is examined after, and leverages everything learned from, evaluation of the client and network portions of the application. Testing steps include: Mobile Web application vulnerability assessment, Mobile SOAP1 or REST2-based Web service testing and Static analysis of any back-end code.
Research-driven methodologies that incorporate industry security standards
Our Mobile Application Security Assessment ensures consistency and repeatability to minimize the risk to systems under test and to cover all the vital areas

Features of our Mobile Application Security Assessment
What sets us apart.
Our recent projects
Innovate wiht Confidence. The data shows why PCI Compliance Services is the right partner for your cybersecurity strategy.
Expertise – When You Need It
what people are saying
See how clients are future proofing their security and Stay ahead of disruption
with PCI Compliance Services

PCI Compliance Services helped us shift to a proactive security stance against threats and meet compliance requirements, giving us greater confidence in our ability to respond to cybersecurity threats faster and more effectively.
Peter Mayers – CEO Quantra Healthcare

PCI Compliance Services deep expertise in cyber procedures and standards identified gaps in our incident response plan and improved our ability to respond to a potential incident.
Smith Ares – CTO Linctron Financials
Get Started
Get in touch with us.
We’re here to help.
Learn more about how our specialists can tailor a security program to fit the needs of your organization.









